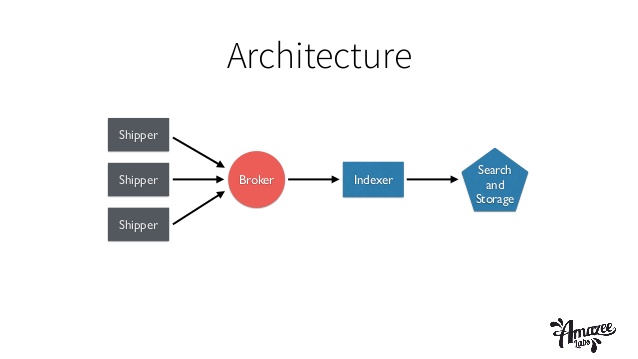
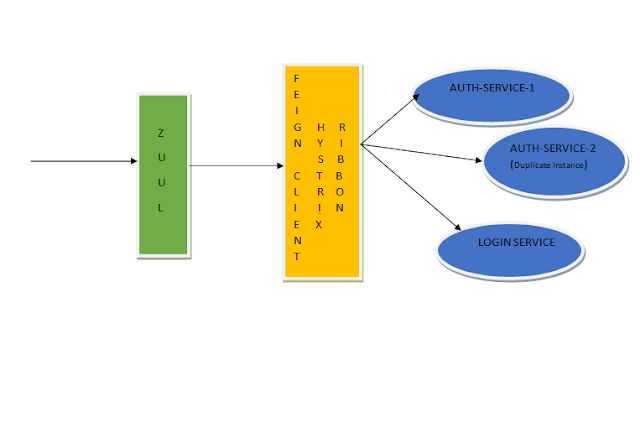
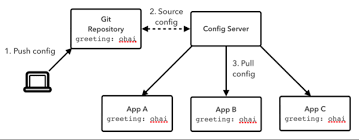
Elastic Search with Spring PART II
1) Index creation or deletion: For Nested Type (Index name is Book) and Parent - Child Relationship (Index name is ParChild) @RequestMapping(value="/addIndex",method = RequestMethod.POST) def addBookIndex(@RequestParam(name = "indexName")String indexName){ logger.info "****** Adding Book Index: $indexName in ELASTIC DB......" def result = elasticsearchTemplate.createIndex(indexName) logger.info "****** Result is: $result " result } @RequestMapping(value="/deleteIndex",method = RequestMethod.POST) def deleteBookIndex(@RequestParam(name = "indexName")String indexName){ logger.info "****** Deleting Book Index: $indexName in ELASTIC DB......" def result = elasticsearchTemplate.deleteIndex(indexName) logger.info "****** Result is: $result " result } 2) Creating Mapping Type Whenever we save a doc